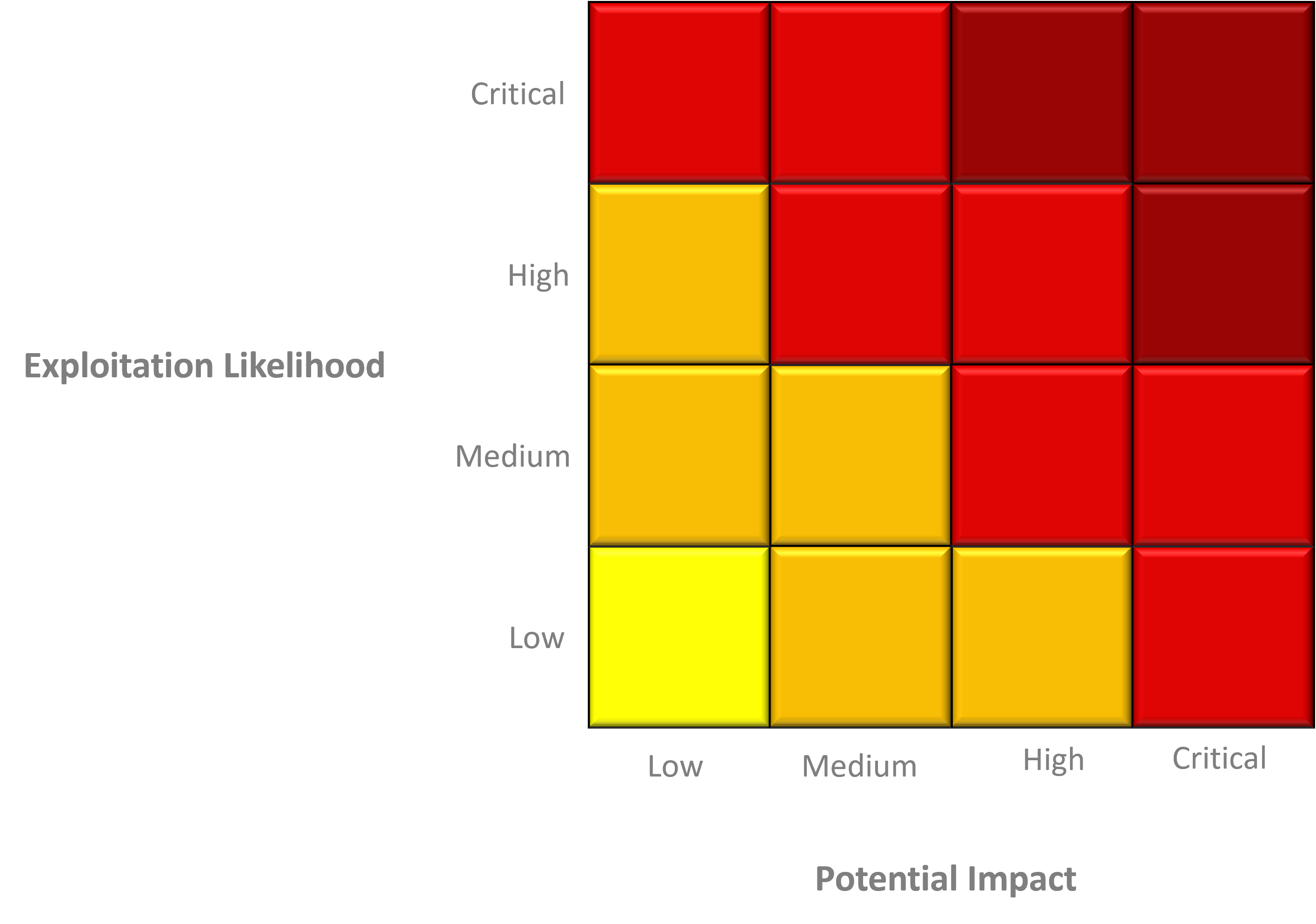
Goal and scope
The purpose of the scoping meeting is to define the objectives of the system audit and to transfer sufficient knowledge about the systems to be tested so that the offer can then be prepared on the basis of this knowledge. The questions mostly revolve around the purpose of the system, different users and roles, test depth and test scenarios.