Ransomware attacks have now become a constant threat that affects every company in Switzerland. Every person should be aware of the danger, and there are no more excuses why not enough has been done to protect the company. The consequences of such an attack can be fatal for any company, regardless of its size. Accordingly, one reads more and more frequently what are the appropriate means and measures against such an attack. The most frequently mentioned measures can be roughly summarized as follows:
- Complex passwords
- 2-factor authentication
- Keeping systems up to date with the help of defined processes
- Backup concept
- Business continuity management (BCM)
- Awareness training for employees, especially for phishing attacks
- Protect external access
- Anti-Virus (AV) and Endpoint Detection and Response (EDR)
These measures are preached over and over again and slowly but surely most people should be aware of them. Of course, these are all good measures and should certainly be implemented by every company. But are these measures really the most sensible ones with the greatest benefit in relation to the effort (see CSROI)? Well, it's a bit more complicated and yet also simpler. It is a fact that the ransom demanded is very often paid and often even still covered by insurance. There are cyber security companies that specialize in negotiating down the demanded sum. The ransomware groups are thus directly financed and must now have a budget that any blue team could only dream of. Accordingly, the attackers' methods are also becoming better and more advanced.
A playbook of the very profitable ransomware-as-a-service Conti was leaked in the last year and has been translated into English in the meantime. Anyone can therefore get an idea of the methods used by such ransomware.
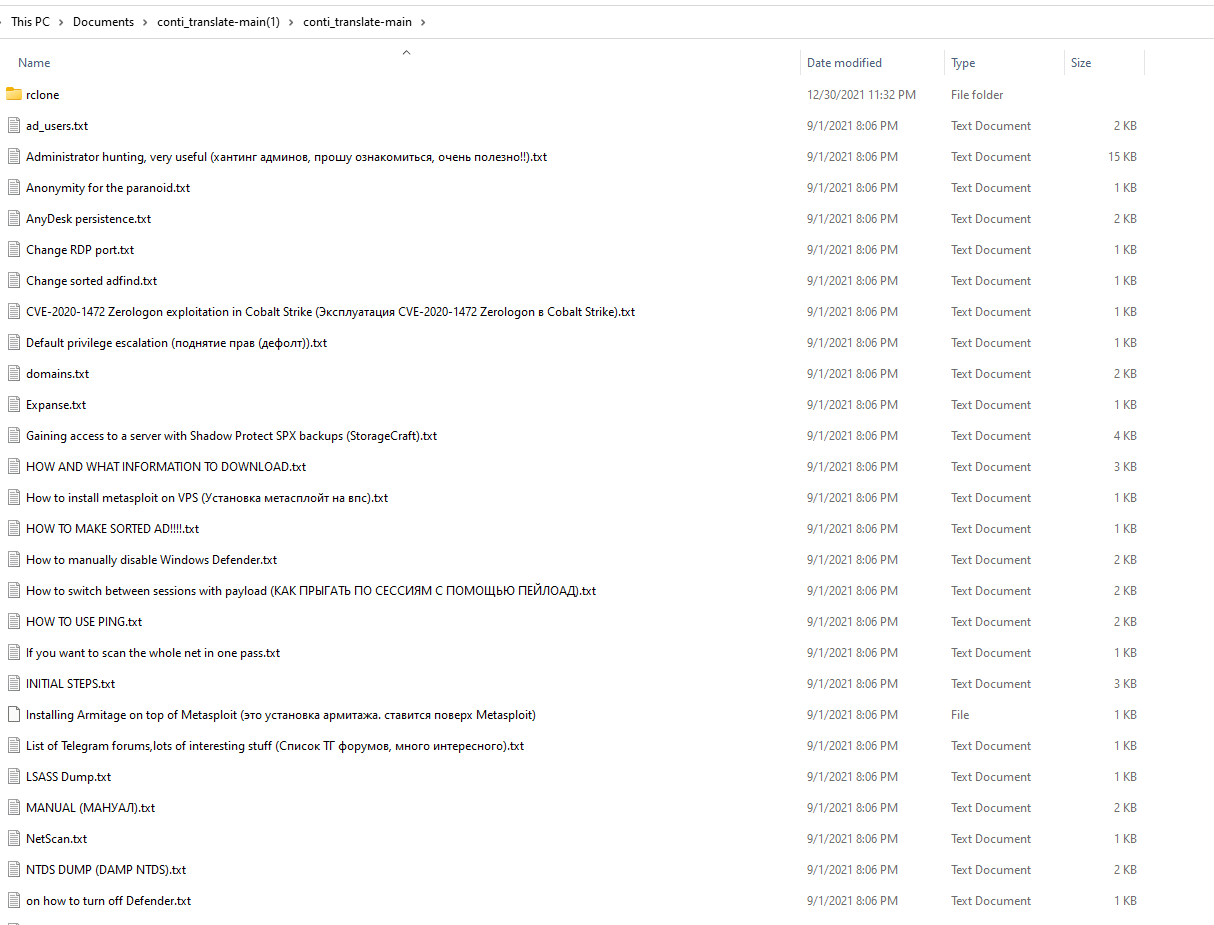
We did this in the course of our research and the methods were frankly surprisingly unsurprising. Practically only known tools and methods are used, as they are public and usable for everyone. Regarding Active Directory Privilege Escalation (a prerequisite for the successful encryption of data), they even simply refer to the following cheat sheet on Github. But the methods show one thing again, which is still largely too little considered: such an attack runs in practically all cases via security-related misconfigurations in the Active Directory. However, the measure of securing the Active Directory did not make it into the list of frequently mentioned measures and is unfortunately considered far too rarely.
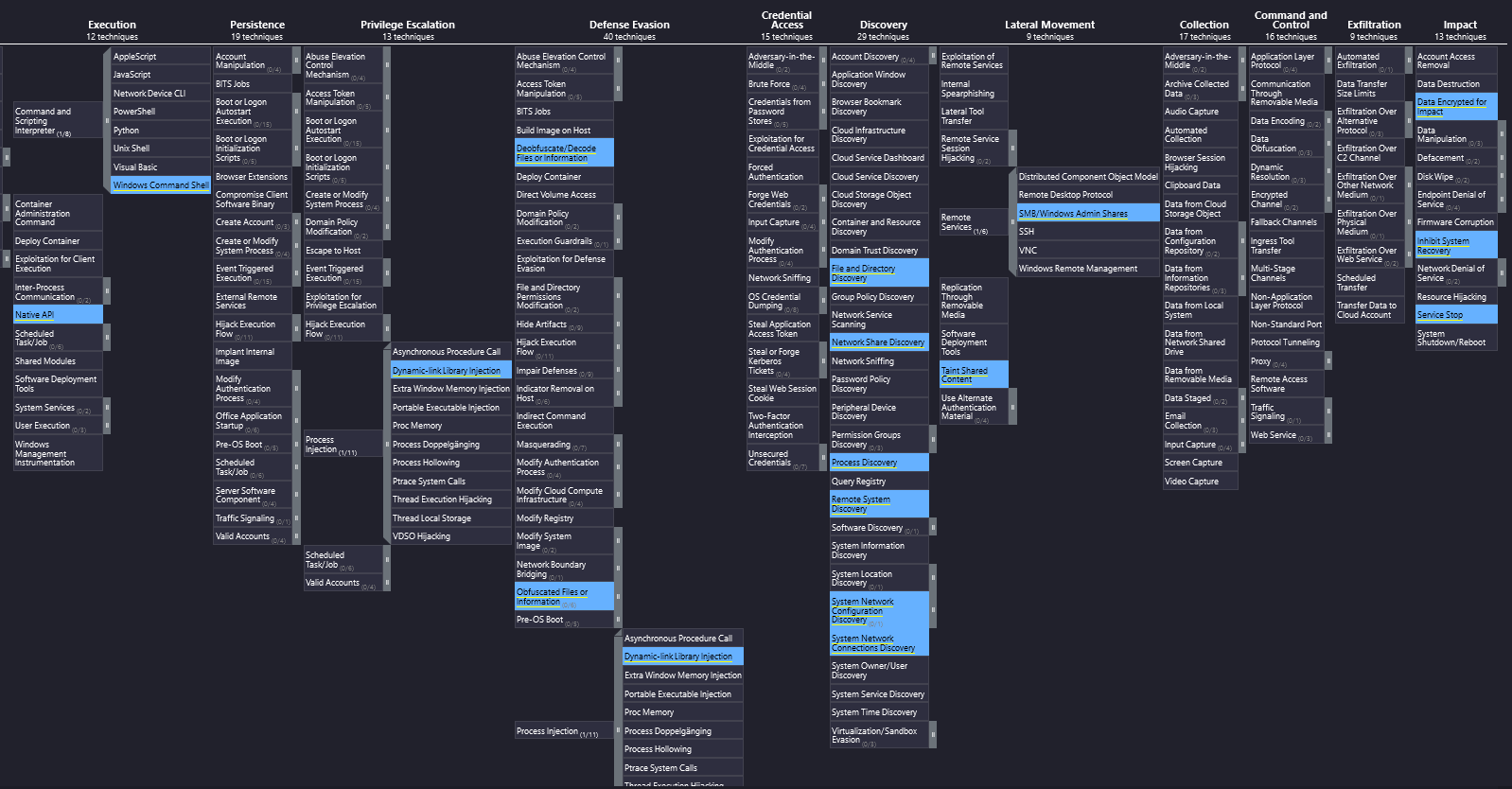
There are the exceptional vulnerabilities such as ZeroLogon (this POC is also referenced in the playbook), which make it so easy for an attacker to not have to deal with Active Directory much. This vulnerability can also be fixed very quickly and easily with patches. Otherwise, a successful ransomware attack should almost always take place via a misconfiguration in Active Directory. The simpler and more obvious such a misconfiguration is, the easier it is for the attacker and the faster a company falls victim to ransomware. Ransomware groups are financially motivated, i.e. they want to collect as much revenue as possible with as little effort as possible. Accordingly, they look for the easiest targets. To exaggerate: You don't have to be perfectly protected as a company, you just don't have to be the easiest target.
So it is precisely because of the weakly configured Active Directory that the company becomes the easiest target, and the frequently mentioned measures unfortunately offer too little protection. That's why we advocate that securing Active Directory should be added to the list of the most important protective measures against ransomware and become an issue for every company. But how can this measure be implemented?
We can turn the tables and use the knowledge of attackers' methods to detect and fix the most easily exploitable misconfigurations. To do this, we can use the same or similar tools as the attackers. One tool that still requires little specific attacker knowledge and delivers results quickly is PingCastle, with the slogan "Get Active Directory Security at 80% in 20% of the time." A company can use the software to audit its own systems free of charge. All one has to do is download the exe file from the website and have an Active Directory user run it. For the cautious: the tool is open source and can be audited and compiled by yourself, so you don't have to trust any executable downloaded from the Internet.
After a few moments, the tool provides an overview of the existing risks, including the domain risk level. The easy-to-use tool thus provides a quick impression of the security situation in the Active Directory and also recommends measures.
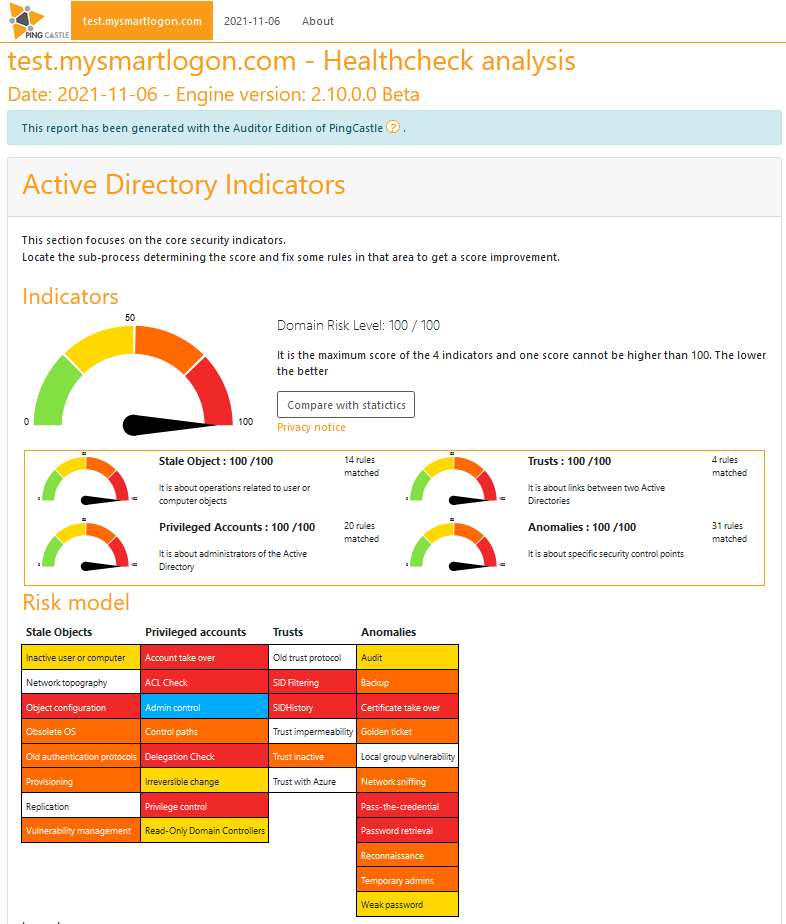
However, the output can also be overwhelming at first and deeper attacker knowledge is helpful in prioritizing and assessing the measures. Other tools that can be used are PowerView and BloodHound, both open source and, according to the playbook, also used extensively by Conti ransomware.
So any company can immediately start this process of securing the Active Directory and thus protecting it from ransomware with little effort. In our "Active Directory Security Improvement" service, we look at exactly these security misconfigurations and help prioritize and assess the measures thanks to our deep attacker knowledge. In this way, a company can stop being the "most lucrative" (easiest) victim for ransomware in the shortest possible time and, with the establishment of an iterative top-down approach, survive in this competition in the long term.