Holistic Information Security Transformation
HIST stands for Holistic Information Security Transformation. HIST offers your organization the opportunity to efficiently transform its cybersecurity from a weakness to a strength. Thanks to the subscription model, improving your security becomes a process that can be scaled flexibly and starts where real danger threatens. Because our career so far has shown: the major security gaps do not show up when a small, specially prepared part of an environment is tested, because it does not reflect reality. The major security gaps show up when we - like an attacker - are allowed to look around, see contexts and processes, and pick the most interesting targets. By allowing us to use our expertise in selecting targets, nothing irrelevant is tested. Thus, resources are saved.
To not only find vulnerabilities, but also provide active protection, HIST is also based on Endpoint Detection & Response (EDR) from our partner CrowdStrike. After the initial purchase, this software protects your endpoints and reports suspicious activities. It also allows you to isolate and investigate them in case of an emergency. The best part is that you don't need people to monitor these reports yourself. We do it for you.
In addition, with us, you also get our knowledge and network involved. For cybersecurity to work in a company, employees need to be trained and made aware. Be it in awareness training or internal training seminars, we pass on our knowledge and make it a point to do this in an understandable way and with lots of demos. If there are areas that we cannot cover on our own, we use our connections to other experts so that these areas are also protected.
HIST is very flexible and we are convinced that we can offer added value to any company.
If the following questions are still open in your company, we recommend HIST:
- How should we go about securing our business against cyberattacks?
- We can't find security specialists, what should we do?
- As an SME, do we really need a full-time position just for our cybersecurity?
- How can we turn our point-in-time safety reviews into a sustained process?
HIST Modules
EDR-as-a-Service
First Response
Vulnerability Management
Attack Path Management
Awareness Campaigns
Knowledge Transfer
Penetration Testing
Red Teaming
Cloud Security
Business Continuity Management
Dark Web Monitoring
And much more
Ganzheitlicher Schutz Ihres Unternehmens
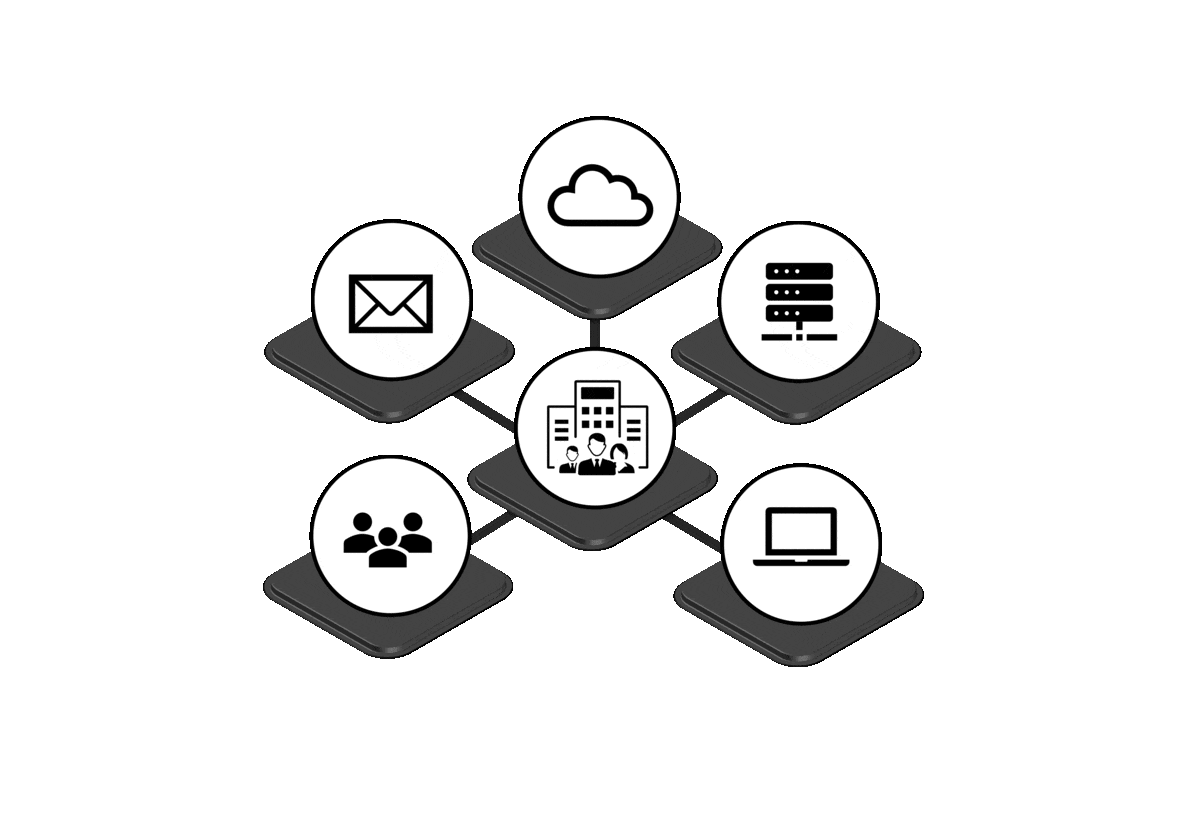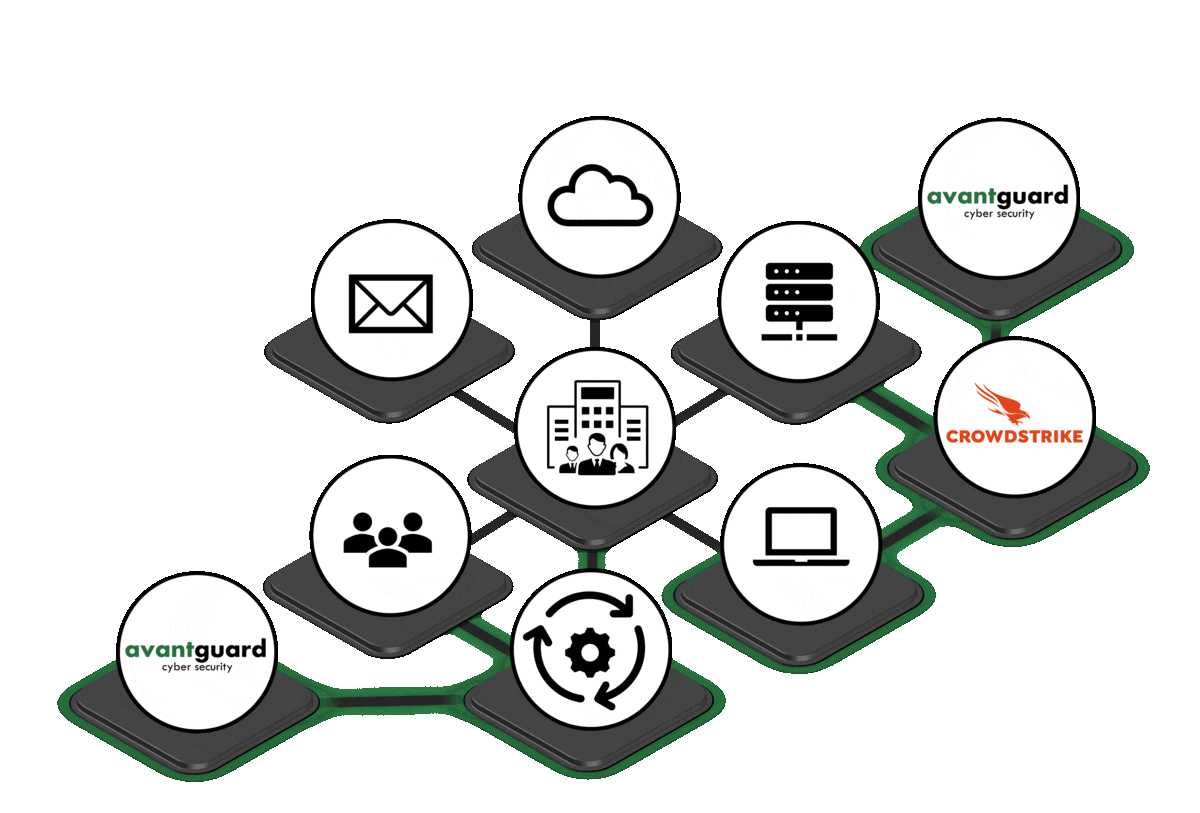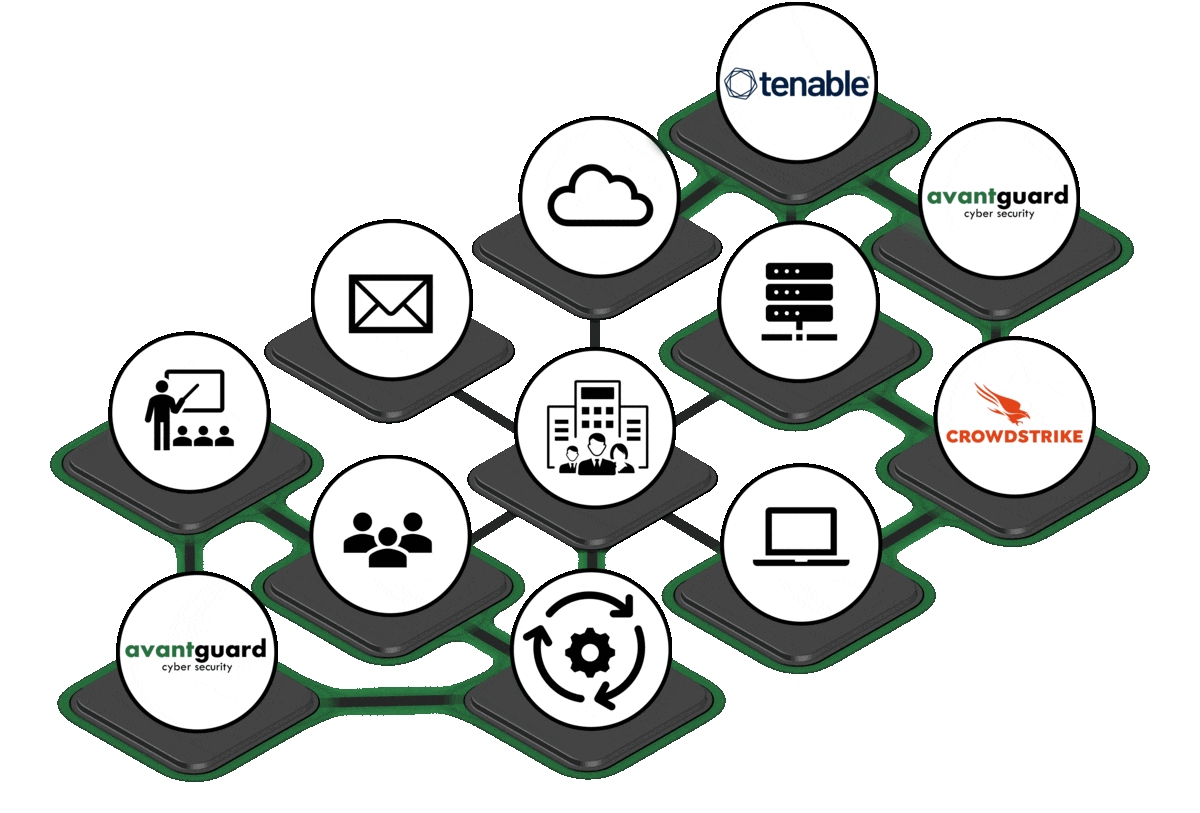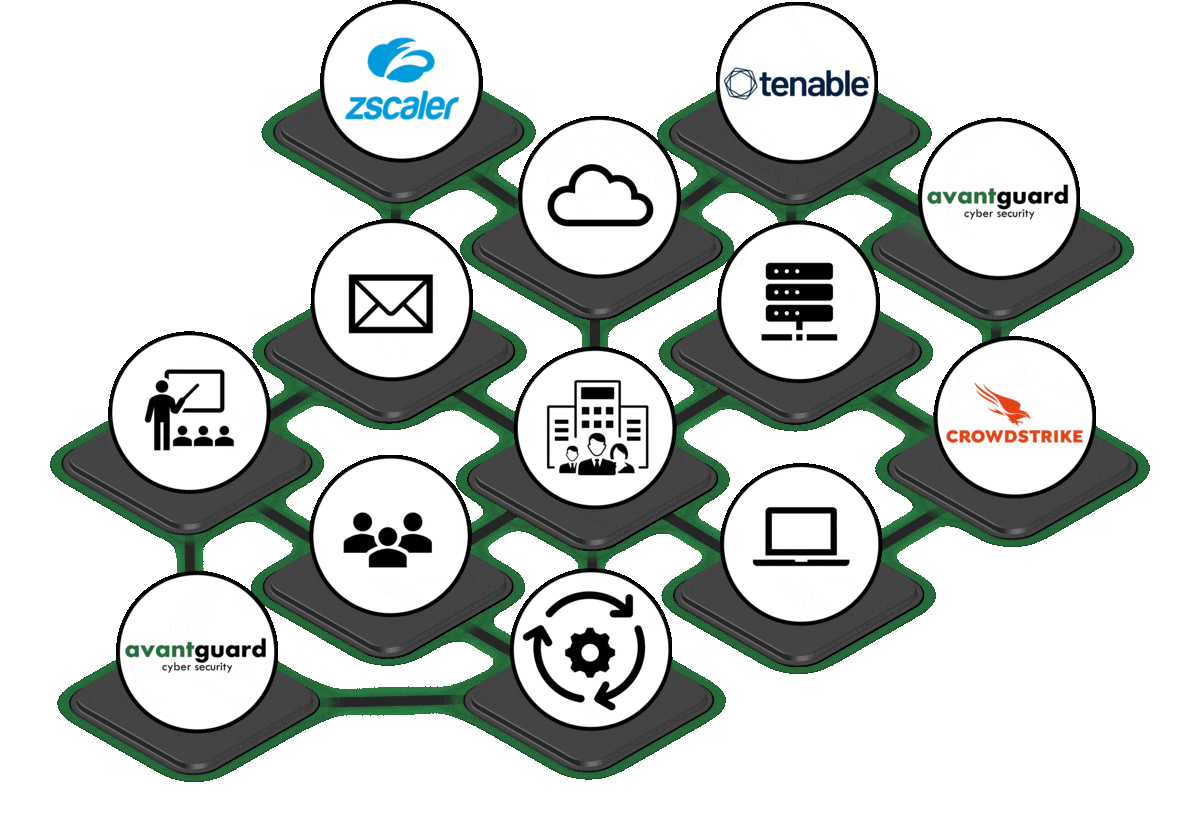
Mesher Platform
Via the Mesher platform, you are constantly informed about your current security level, all measures and costs. Here, all threads come together and you keep the overview and control. There are no hidden costs and you can keep an eye on your company's progress thanks to measurability. Thanks to the central platform, results and findings can be implemented as efficiently as possible and bottlenecks and media breaks can be prevented.



