Passwords and their secure management continue to cause major problems for many companies. There are numerous recommendations regarding the complexity of passwords. With the amount of different and secure, and therefore complex, passwords, it is practically impossible to remember them and the use of a password manager becomes almost mandatory. For this purpose, many companies use the open source password manager KeePass. This simplifies the administration of passwords massively, but offers numerous attack possibilities in the default configuration. In this blog, these attack possibilities are shown and also hardening measures in KeePass to counteract them.
To show the possible attacks, we install the latest version (2.49 on 09/30/2021) of KeePass and create a new database with a master password in the default configuration. If an attacker finds such a database (.kdbx), he can transfer it to himself and use keepass2john (part of John the Ripper) to extract the hash of the master password, which can then be cracked with Hashcat or John the Ripper.
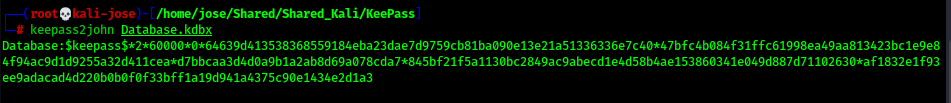
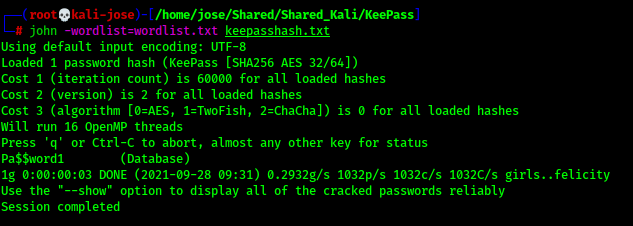
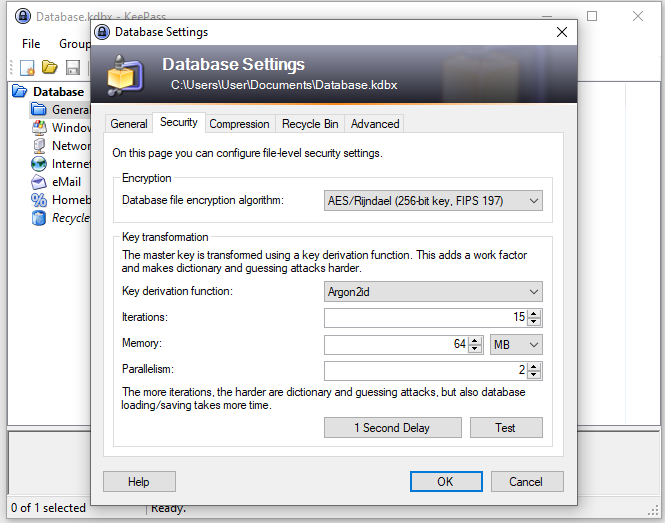
Cracking the password depends, of course, on whether the password is in the word list used. Nevertheless, cracking can be made much more difficult by setting the key transformation to 1 Second Delay (File -> Database Settings -> Security tab). By clicking the '1 Second Delay' button, KeePass calculates the number of iterations that result in a one second delay when loading/saving a database. This massively reduces the performance of cracking and the key derivation functions Argon2d and Argon2id are not even currently supported by keepass2john. Thus a possible cracking can be counteracted effectively.
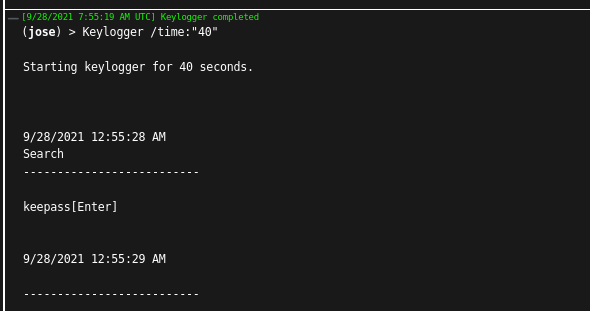
Another possibility for an attacker is to use a keylogger. For a short proof-of-concept we use the keylogger task of the command-and-control framework Covenant and reading the master password is easy.
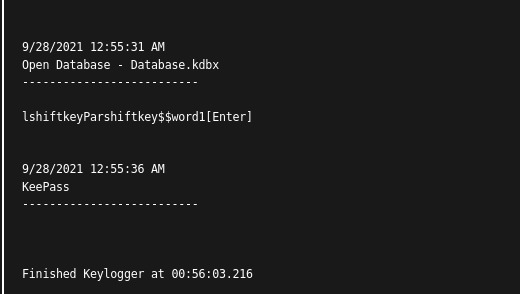
Fortunately, this attack can also be prevented relatively easily. Just check the checkbox Tools -> Options -> Security Tab -> Advanced -> Enter master key on secure desktop and the master password cannot be read by a keylogger.
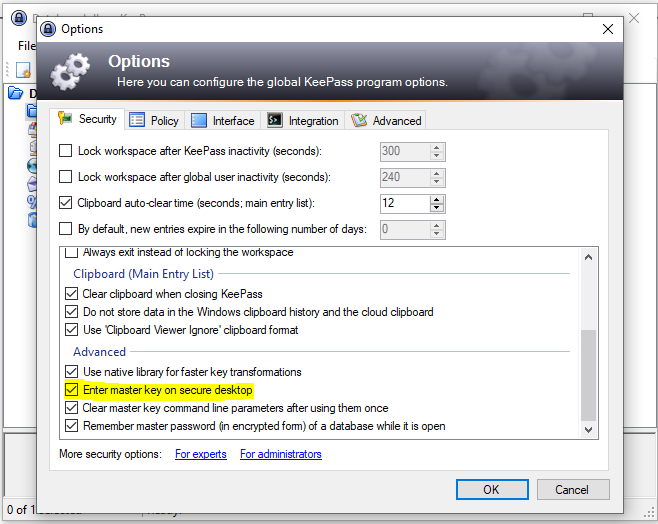
The tool KeeThief offers another possibility to read the master password from the working memory. To do this, the KeePass process must be running, the database must be decrypted, and the attacker must obtain code execution in the context of the user. However, no local administrator privileges are required for this.
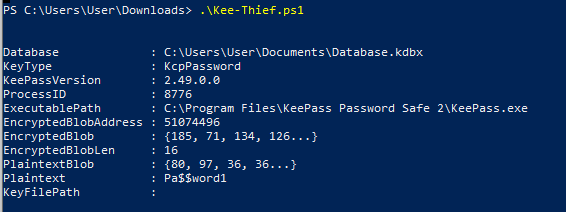
Successful execution of the KeeThief tool can also be prevented with an option, this is Tools -> Options -> SecurityTab -> Advanced -> Remember master password (in encrypted form) of a database while it is open, which should be disabled.
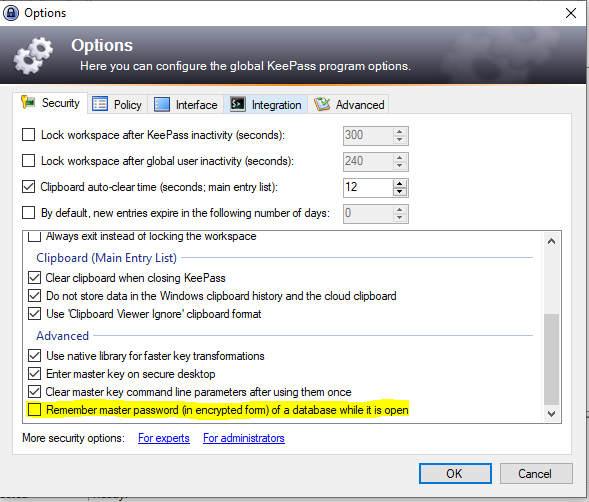
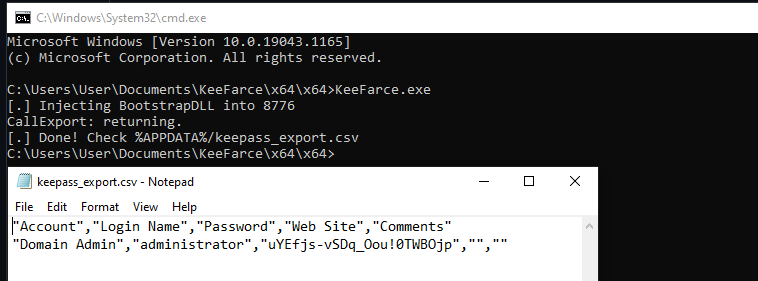
Although this at least prevents the KeeThief tool from running, it does not solve the basic problem that makes such attacks possible in the first place. The KeePass process runs in the user's context, and thus it can be accessed in the same context. The KeeFarce tool takes advantage of this to use DLL injection to achieve code execution in the context of the KeePass process and then read the passwords in the KeePass database.
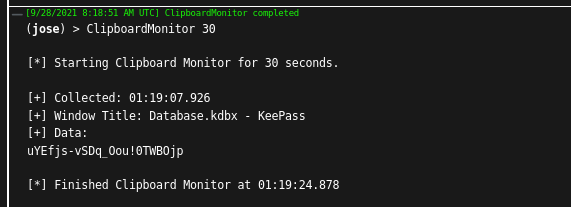
Also, actively used passwords from KeePass can still be read very easily with Covenant's ClipboardMonitor. The ClipboardMonitor shows an attacker what the user copies from which window to his clipboard. Since KeePass allows a password to be placed on the clipboard for a short time, it appears in plain text in the output.
In summary, a password manager such as KeePass solves the basic problem regarding the handling of complex passwords and allows meeting the requirements for their complexity. Therefore, its use is highly recommended. However, new attack surfaces and risks always arise with the introduction of software. The hardening measures highlighted in this blog can counteract some well. These measures are:
- Key Transformation Settings
- Secure Desktop Setting
- Remember Master Password Setting
Even if these measures do not prevent all attacks, they make it considerably more difficult to attack KeePass and are therefore very sensible measures. Awareness of the remaining risks of KeePass despite hardening enables further, holistic measures to be taken to protect the organization.