Threadless Ops - Enhanced Shellcoding for Threadless Injections
Process Injection is essential in red teaming and serves various strategic objectives, enabling attackers to expand their capabilities.
About Red Teaming and what actually constitutes a good Red Teaming.
The term Red Team originates from the military and refers to a group that takes the role of the attacker in an exercise. Opposite the Red Team is the group of defenders, the Blue Team. These terms can be transferred very well to cyber security and thus also provide the two core elements of a Red teaming, in which a Blue Team always participates. In cyber security, however, the terms tend to be somewhat watered down and no clear definition exists. We (and many other experts) make a clear distinction here between penetration testing, which for example can also be performed on an entire company and Red Teaming. The rule is actually relatively simple: if a company does not have a Blue Team, it does not need a special procedure (OPSEC) to test and measure the reactions of the Blue Team. Thus, a more efficient penetration test can be performed. However, the tactics, techniques and procedures (TTP) used can be very similar to those of a Red Team. If a Blue Team is present, it is an essential part of a Red Teaming and the operations of the Red Team are aligned with the target, namely training and measurability for the Blue Team.
Now that the terms Red Teaming and penetration test have been delineated, the question arises as to what actually constitutes a good Red Teaming. Basically, good Red Teaming is characterized by the fact that Red Teaming improves the Blue Team. Period. It should never be the goal of a Red Team to demonstrate superiority. A supposedly successful Red Teaming, i.e. all set goals were achieved (for example the achievement of Domain Admin privileges), can still be a bad Red Teaming, because no new knowledge was gained for the Blue Team and thus it could not be improved. Therefore, a realistic threat should be chosen as the basis of any Red Teaming and this threat should be imitated as closely as possible. This imitation can and should also retain obvious weaknesses of the real threat. An example to explain: a ransomware group always uses the same tool, which generates a clear Indicator of Compromise. Of course, it is easy for a Red Team to avoid these very indicators. But doing so destroys precisely one of the most important insights for the Blue Team, namely whether this real threat could be detected. Such indicators should be deliberately retained by the Red Team. Of course, depending on the Blue Team's maturity, certain factors could be changed to adapt the Red Teaming to the Blue Team's capabilities. The choice of the real threat is the basis for the success of the Red Teaming and accordingly enough time should be spent on it. This can be done relatively easily with the MITRE ATT&CK® framework. Here, real threats can be selected and their tactics, techniques and procedures can be studied and used and adapted for Red Teaming.
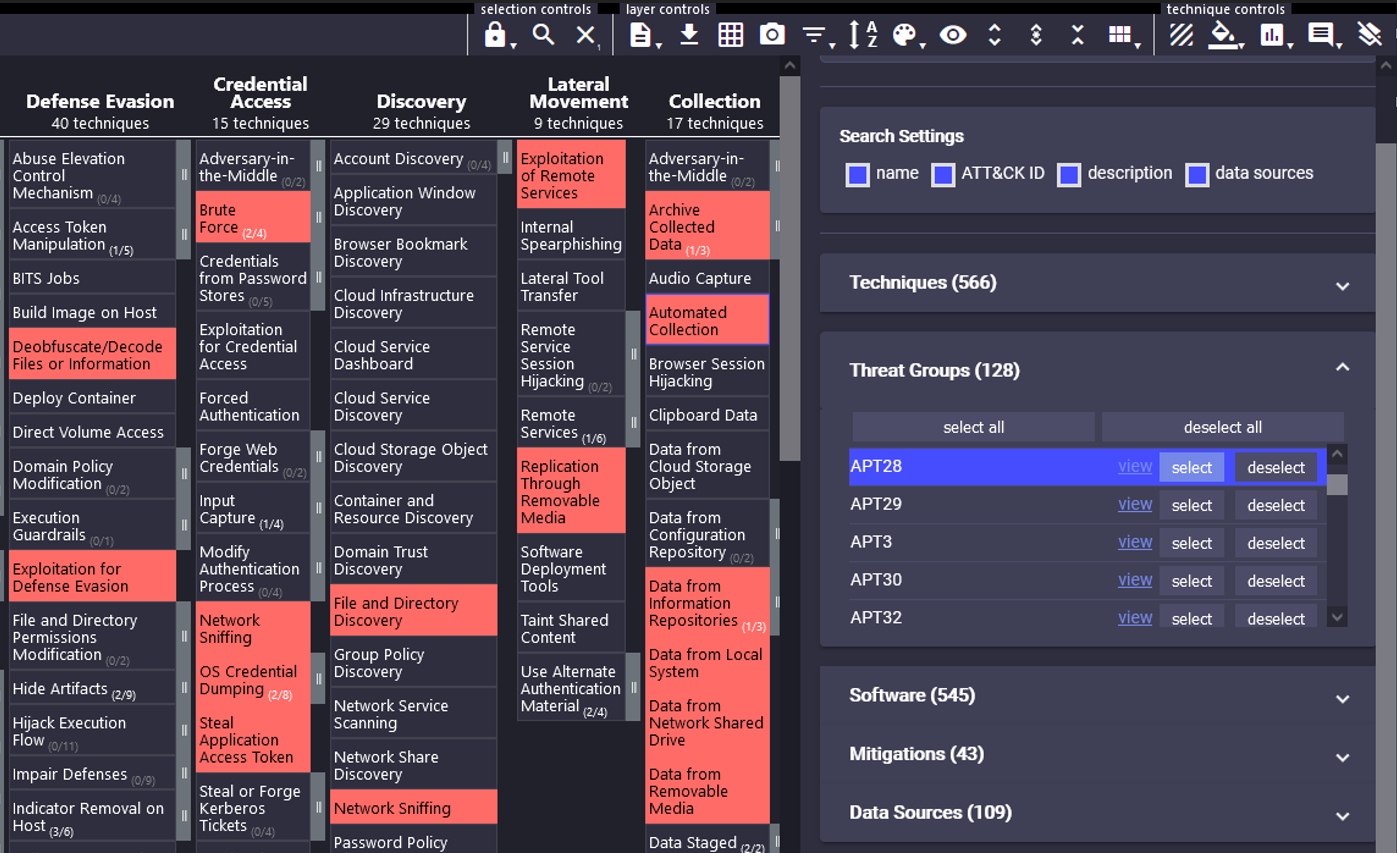
Since it is always a simulation, certain parts of the attack chain can also be simulated. For example, if a supply chain attack is to be simulated, the Red Team obviously cannot attack a supplier to perform this type of attack. However, the injection of malicious code into procured software can be recreated and thus simulated with relative ease. These targeted simplifications can enable very efficient and successful Red Teamings. Another example is the widely used Assume Breach approach, which is already successfully used in most Red Teamings.
For both Red Team and Blue Team, the choice of Command and Control (C2) infrastructure is of utmost importance. There is a clear trend here and most of the time both teams are very fixated on Cobalt Strike. This may make sense according to real-world threat observations and the frequent use of Cobalt Strike. However, survivorship bias must be factored in here, as well as other real-world threat findings. Survivorship bias refers to a cognitive bias. According to survivorship bias, probabilities of success are systematically overestimated because successful people or states are more visible than unsuccessful ones (https://en.wikipedia.org/wiki/Survivorship_bias). With this predominant fixation on Cobalt Strike, it is also absolutely clear that its use can be detected most often. The detection of other C2, such as the open source C2 Covenant, which is used very successfully by avantguard cyber security and has also been further developed, can be many times more difficult. For example, Covenant was also used very successfully by the APT group HAFNIUM (https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/). But these are exactly the most dangerous threats, threats which are not yet well studied or even discovered. These factors should also be factored into a good Red Teaming, especially for Blue Teams with greater experience.

Regardless of how advanced a threat is, there will always be moments in the course of an attack chain when the attacker must take some risk with respect to OPSEC in order to achieve the defined end goal. And it is these decision points that are critical for both the Red and Blue Teams. This is where the Blue Team has the best opportunity to detect an attack, regardless of chosen tactics, techniques, and procedures. In good Red Teaming, a special focus is placed on these points in the attack chain and the Blue Team's ability to detect an attack, whether real or simulated, is improved right here.
Now numerous factors have been mentioned, which make up a good Red Teaming. So how does avantguard cyber security ensure good Red Teaming?
The technical skills of the Red Team operator are a basic requirement for a successful Red Team, but how can these be ensured? There are very good trainings in this area including certificates which can be obtained. Hands-on courses and exams are much more meaningful than multiple-choice exams. There is the famous OSCP (Offensive Security Certified Professional), which has to be achieved in a notorious 48 hour exam (24 h hacking and 24 h report writing). The next step up from the OSCP is the OSEP (Offensive Security Experienced Penetration Tester), which must be achieved in a 72 hour exam (48 h attacking, 24 h report). The associated training Evasion Techniques and Breaching Defenses including Hands-on Lab provides the necessary equipment for the exam, which is nevertheless very demanding and simulates a penetration test on an entire company. Zero-Point Security's CRTO (Certified Red Team Operator) covers numerous attacks and the use of C2 frameworks such as Covenant and Cobalt Strike. The certificate must be obtained in a 48-hour exam (48h attack, without report). The CRTP (Certified Red Team Professional) with the course Attacking and Defending Active Directory from Pentester Academy must also be obtained in a 72 hour exam (24 h attacking, 48 h report) and deals mainly with Active Directory, which is of immense importance in all courses and also in real attacks. Furthermore, there is the platform Hack The Box including Academy and Pro Labs. In the Pro Labs, penetration tests and Red Teamings can be simulated on holistic infrastructures of companies. Of particular note here is the Pro Lab Cybernetics, which corresponds to Red Team Operator Level 2 and is a real challenge with 28 machines and numerous domains, and is better hardened than probably most companies in the real world. All the mentioned certificates and courses have been successfully completed by avantguard cyber security employees and prove the technical competence.

All avantguard cyber security employees have an academic background. This is particularly evident when it comes to processing the findings from a Red Teaming and passing them on to the Blue Team. A scientific approach makes it easier to gather the most important findings and enables targeted communication and collaboration with the Blue Team. A basic understanding of computer science helps to understand and account for the many digital processes in an organization.
However, "textbook knowledge" cannot always be transferred 1-1 to the working world and this is where experience comes into play. Numerous, successful Red Teamings have been led and conducted by avantguard cyber security staff. The knowledge about what distinguishes a good Red Teaming from a bad one has always been of the greatest benefit and has proven itself anew. In a company, numerous factors come together, which in particular also influence the Blue Team and their working methods and performance. These factors must also be taken into account when working through Red Teaming in order to improve the performance of the Blue Team as a whole.
Finally, it is a question of how these findings are transported to the Blue Team and the company as a whole. In the end, the final report is what remains. Again, using the ATT&CK matrix as a common language between Red and Blue Team has proven to be effective. With the assignment in the matrix, more in-depth, independent research by the Blue Team is also made possible. Additionally, by using the matrix in an iterative process, an organization's Purple Team coverage can be measured and improved. In this process, both the Red and Blue Teams maintain a matrix and mark the techniques for which operations have already been performed or measures implemented from the perspective of the respective team. The overlaps (blue + red = purple) show the techniques that have already been tested on both sides. This combined matrix can now be used to plan the next steps. Blue fields (marked by the Blue Team) should be considered in future operations by the Red Team and the measures tested. For red fields (marked by the Red Team), the Blue Team should consider measures. For purple fields (marked by both teams), the techniques can be refined, but there is already mutual verification of the implemented measures. For the unmarked fields, the company is so far "blind", these should be considered by both teams. Prioritization of techniques can again be achieved with threat analysis. Purple Team coverage should be maximized iteratively to protect the enterprise as comprehensively and deeply as possible.
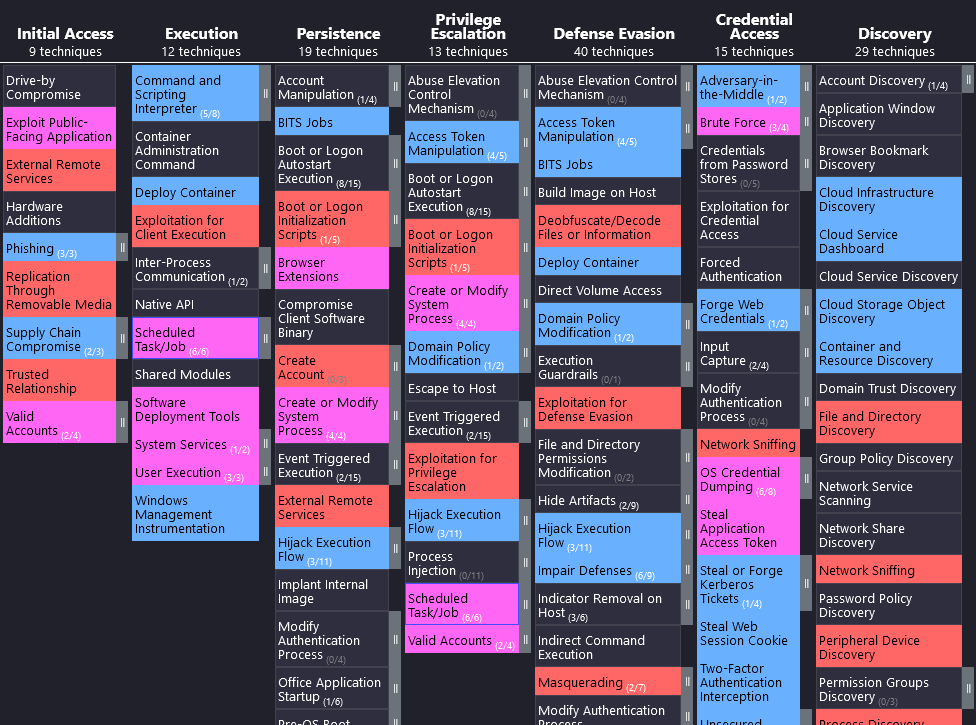
A final report alone, no matter how well and comprehensibly written, is still difficult to understand without additional context and deeper knowledge due to the complexity of the subject matter. Therefore, avantguard cyber security is always available for explanations and follow-up questions. In the end, it is not the final report that protects against real attacks, but the findings and their implementation in the company.
With avantguard cyber security, all these factors come together. In a Red Teaming, a suitable scenario is first defined and the implementation is planned based on the capabilities of the Blue Team, including definition of the characteristic Indicators of Compromise and critical points for detection in the attack chain, using ATT&CK. Red Team operators bring their technical and academic knowledge to Red Teaming to ensure successful and targeted execution. Great importance is given to the follow-up and the transport of the findings into the company in order to achieve the one big goal, the improvement of the Blue Team and thus the security of the company.
Sources (books):
Process Injection is essential in red teaming and serves various strategic objectives, enabling attackers to expand their capabilities.
What Really Helps Against Ransomware Analysis of the methods of Conti ransomware
In this blog post, we show the steps necessary to recreate attacks on AD CS in a test environment. We also show how defenders can identify potential...