Core Security Return on Investment
In order to improve the cyber security in a company, investments are needed. As with every investment in a company, the question arises as to how investments can be made in the most sensible way. In business management, the key figure return on investment is often used for this purpose. A similar principle can also be applied in cyber security, the Core Security Return on Investment (CSROI) as defined by us. Core Security in this context means a protection mechanism that can protect the company from an actual attack, where it can add the most damage to the company. Estimating the core security return on investment is not always trivial and requires in-depth knowledge of current attack methods and how to protect against them efficiently. Nevertheless, estimating the CSROI should play an important role in deciding where the cyber security budget can be best and most efficiently spent.
As an example, consider a company that has spent a lot of money on an expensive firewall with network inspection using the latest technology with AI and machine learning, regularly conducts awareness training, and as part of a consultation, an inventory was created and all known risks were recorded and cataloged. Despite the costly investment, however, the heart of internal IT, Windows Active Directory, was left out of the process. Despite awareness training, the automated ransomware reaches an internal system via spear phishing. Further communication is encrypted with domain fronting and even the most sophisticated network inspection cannot inspect all data traffic and detect command and control communication for compliance reasons. The further path to the Domain Admin is a piece of cake due to the weakly configured Active Directory and a total loss occurs due to the successful automated ransomware attack.
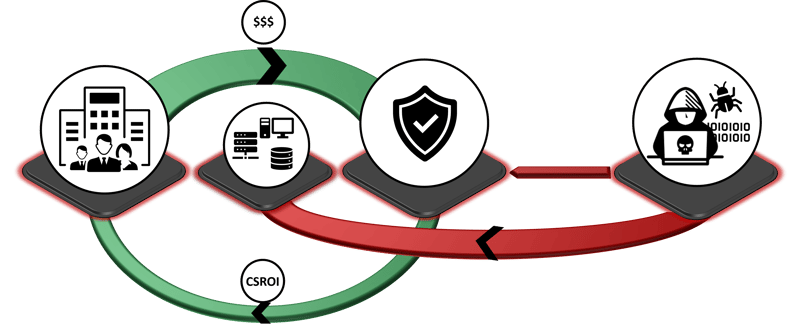
In contrast, another company specifically invested its limited resources in an Active Directory Security Check and weeded out the most common misconfigurations. Despite successful spear phishing, the malware is unable to spread throughout Active Directory and the attackers prefer to pounce on an easier target, which in this case, despite massively higher investments, is the former company.
This extreme example shows how different the core security return on investment can be and why it makes sense to think extensively about how the budget can be invested most sensibly. In these considerations, the attacker's perspective is indispensable and we can help your organization maximize your CSROI and make the most sense of the available cyber security budget.
In order to improve the cyber security in a company, investments are needed. As with every investment in a company, the question arises as to how investments can be made in the most sensible way. In business management, the key figure return on investment is often used for this purpose. A similar principle can also be applied in cyber security, the Core Security Return on Investment (CSROI) as defined by us. Core Security in this context means a protection mechanism that can protect the company from an actual attack, where it can add the most damage to the company. Estimating the core security return on investment is not always trivial and requires in-depth knowledge of current attack methods and how to protect against them efficiently. Nevertheless, estimating the CSROI should play an important role in deciding where the cyber security budget can be best and most efficiently spent.
As an example, consider a company that has spent a lot of money on an expensive firewall with network inspection using the latest technology with AI and machine learning, regularly conducts awareness training, and as part of a consultation, an inventory was created and all known risks were recorded and cataloged. Despite the costly investment, however, the heart of internal IT, Windows Active Directory, was left out of the process. Despite awareness training, the automated ransomware reaches an internal system via spear phishing. Further communication is encrypted with domain fronting and even the most sophisticated network inspection cannot inspect all data traffic and detect command and control communication for compliance reasons. The further path to the Domain Admin is a piece of cake due to the weakly configured Active Directory and a total loss occurs due to the successful automated ransomware attack.
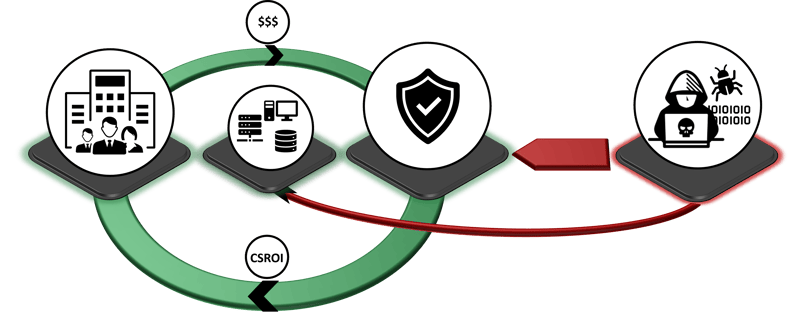
In contrast, another company specifically invested its limited resources in an Active Directory Security Check and weeded out the most common misconfigurations. Despite successful spear phishing, the malware is unable to spread throughout Active Directory and the attackers prefer to pounce on an easier target, which in this case, despite massively higher investments, is the former company.
This extreme example shows how different the core security return on investment can be and why it makes sense to think extensively about how the budget can be invested most sensibly. In these considerations, the attacker's perspective is indispensable and we can help your organization maximize your CSROI and make the most sense of the available cyber security budget.


