Since I didn't find a detailed review before I started the lab, I decided to write one myself. There are also two tips at the very end.
TL;DR The lab is highly recommended, but definitely not for beginners.
Briefly about my background, I completed Pro Lab Cybernetics, Offensive Security Certified Professional (OSCP), Offensive Security Experienced Penetration Tester (OSEP), Certified Red Team Professional (CRTP), Certified Red Team Operator (CRTO), Certified Azure Red Team Professional (CARTP), and Virtual Hacking Labs Advanced+ before APTLabs.
Hack the Box's Pro Lab APTLabs is the most difficult of the Pro Labs, is rated Red Team Operator Level 3, and is called the "Ultimate Red Team Challenge." The lab can be solved on the Hack the Box platform at the following prices:
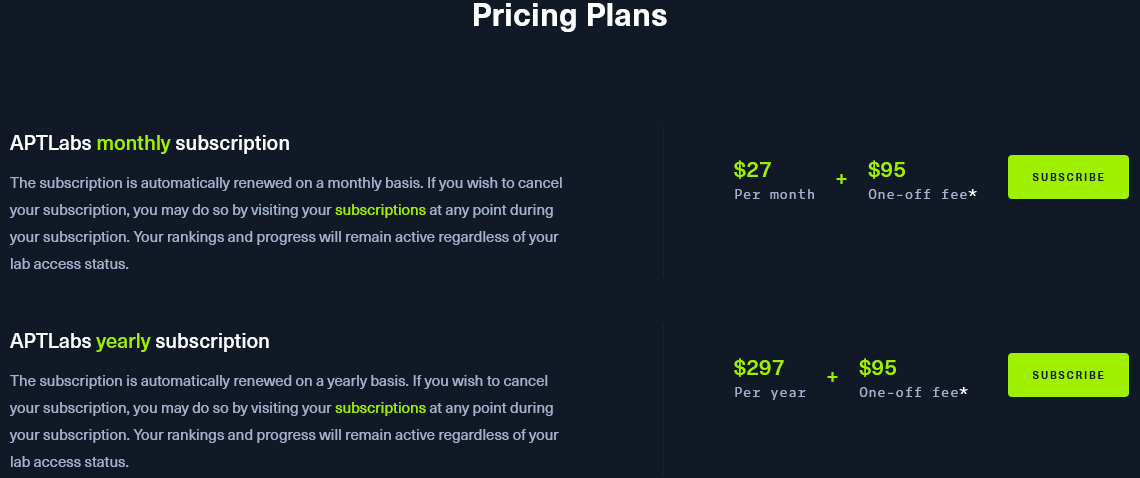
Compared to other courses/labs, the Pro Lab is relatively inexpensive, but you are not taken by the hand. You are completely on your own and all knowledge about modern attack paths in Active Directory must be acquired and used yourself. The lab, as expected at the highest difficulty level, also requires a great deal of knowledge in many areas and a willingness to read up on new attack methods and cyber security research. Basically, the network must be compromised without exploiting any CVEs. Only the names of the flags, 20 of which have to be collected on 18 different machines, sometimes provide some assistance. Even though the flags don't necessarily have to be collected in the given order, if you follow the intended path, they are in the correct order. However, there seems to be multiple intended paths, which can confuse the order somewhat. A small suggestion for improvement can be made at this point. Although the lab is still relatively new (release 01.12.2020), a lot has of course been done in terms of vulnerabilities and this allows in some places to take an easier path. Of course, it is your own fault if you use these "simplifications", however, the temptation is sometimes high, especially if you are blocked somewhere. Maybe some patches could be applied here and there.

The attack paths are overall very interesting and varied and include attacks that you might have read about and can actually be used here, which is of course very cool. Technologies are exploited that are also very widespread outside the lab. Accordingly, the techniques learned are also very relevant to real Red Teamings in real companies. However, there is no Blue Team in the lab that actively acts against the Red Team operator to prevent any misunderstandings. However, there are various modern security features that are in use in the lab and have to be bypassed. In the vast majority of companies, the compromise should not be nearly as demanding as in this lab.
It is recommended to use a command and control (C2) framework for the lab. While I used the open source C2 Covenant for the Pro Lab Cybernetics and was very happy with it, I used Cobalt Strike for APTLabs and was also very happy. The Socks Proxy in Cobalt Strike simplified my life a few times.
The lab is completely reset once per day and all progress is lost. Of course, this is a bit annoying, but if you dump the right hashes and use tools, you can get back to the same point relatively quickly without having to re-run all the attacks. In return, the Lab is very stable overall and practically all attacks work reliably.
As already mentioned, there is no help from Hack the Box apart from the names of the flags and you are completely on your own. However, there is a prolabs-aptlabs channel on Hack the Box's Discord server where you can ask for help. Since the number of people working on the lab is very small, you also have to be a bit lucky and find the right people.
In summary, I can warmly recommend the lab to anyone who has the necessary know-how and, above all, the motivation and will. It is probably the most difficult lab that exists in this field. If anyone knows of something more challenging, I'd love to hear about it. 😉 Accordingly, it also feels good when you've collected all the flags and received the certificate.
Finally, as promised, two tips:
- Cracking hashes sometimes requires more than just using the well-known Rockyou.txt word list, very helpful are these Hashcat rules: https://github.com/NotSoSecure/password_cracking_rules
- Relaying attacks are an important part of the lab and it helps a lot to know different ways to manipulate DNS records to make such an attack possible.